Configure Secure Shopping
- Comodo Secure Shopping provides unbeatable security for online banking and shopping sessions by ensuring you connect to those websites from within a dedicated, security-hardened browsing environment.
- You also have the option to create alerts when you visit certain sites, so you can choose whether or not to open the site in the secure environment.
In addition to websites and browsers, you can also run any 'regular' application inside Secure Shopping. This is especially valuable for applications that process sensitive data, such as:
- Email applications like Outlook and Thunderbird
- Accounting software like Tally and Sage
- Password managers
- Spreadsheet software like Excel and Open Office Calc
- FTP and VPN clients
- Instant messaging and chat applications
- File sharing clients like Drop Box
Configure Secure Shopping
- Click 'Settings' on the CIS home screen
- Click 'Advanced Protection' > 'Secure Shopping'
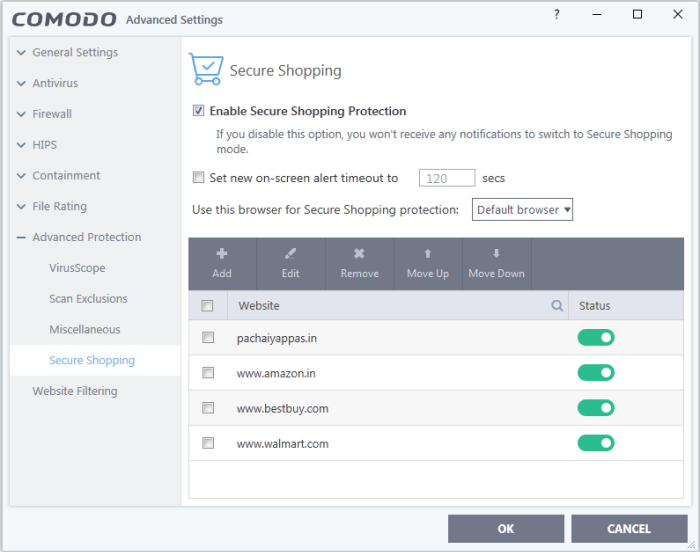
- Click the 'Add' button then type the URL of the site you want to visit securely:
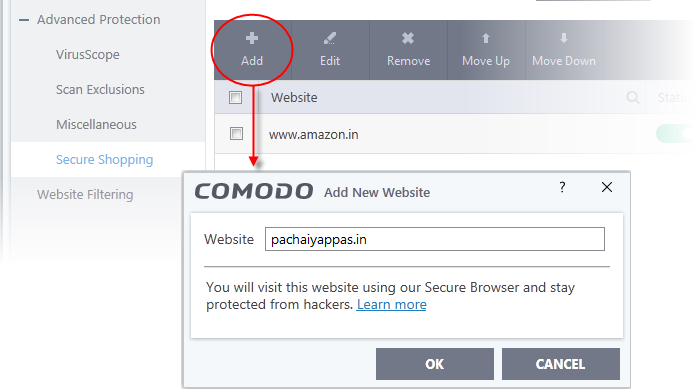
- Click 'OK' to add the site to the list. Repeat the process to add more sites
- Click
'OK' in the 'Advanced Settings' interface to save your changes
An alert is shown if you visit a site on the secure shopping list:
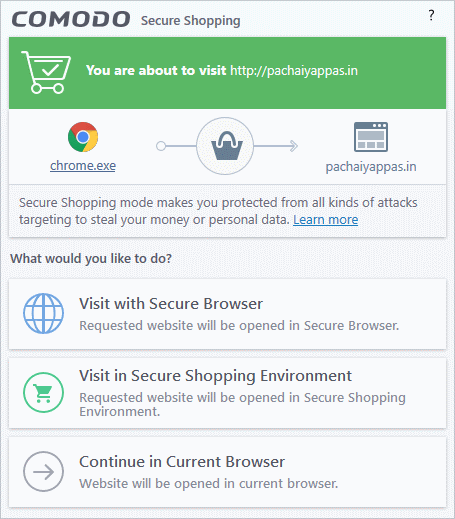
- Choose how you want to proceed:
- Visit with Secure Browser - The site opens in a browser protected by all secure shopping technologies except full process isolation. Full process isolation is replaced with partial process isolation. The browser window will have a blue border around it:
Use Comodo Secure Shopping Environment
- Visit in Secure Shopping Environment - The website opens in a security hardened, virtual environment. When inside this environment, your browser cannot be accessed or potentially attacked by other processes running on your computer. The environment also features a virtual keyboard which allows you to enter confidential information without fear of your keystrokes being tracked. See Use Comodo Secure Shopping Enviroment for more details.
- Continue in Current Browser – Resume your browsing activities with the same browser through which the website was opened. See ror more details on the Secure Shopping Environment.
The 'Secure Shopping' environment automatically opens when you choose 'Visit in Secure Shopping Environment' in the 'Secure Shopping' alert.
You can manually open the 'Secure Shopping' environment in the following ways:
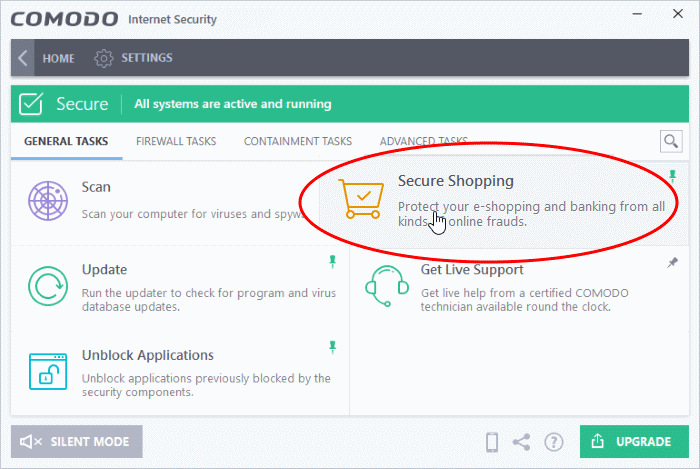
- CIS Home Screen - Click 'Tasks' > 'General Tasks' > 'Secure Shopping'
- CIS Desktop Widget - Click the 'Secure Shopping' icon from the CIS desktop widget
- Windows Start menu - Click Windows Start/Home > All Programs > Comodo > Comodo Secure Shopping
- Windows Desktop icon - Double-click the 'Comodo Secure Shopping' shortcut on the desktop

When you start the application, a welcome screen will appear which explains the benefits of secure shopping:
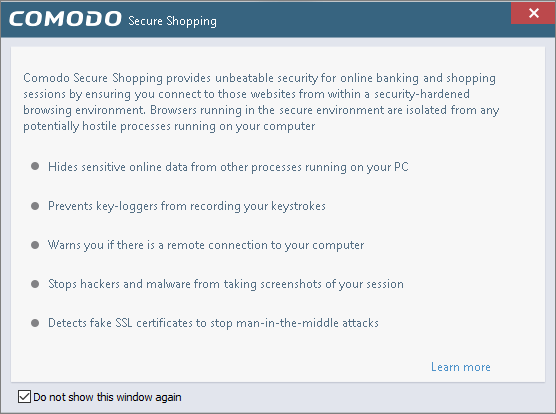
- Check
'Do not show this window again' to
disable the welcome screen in future.
Shopping
and Banking Activities
- If you are visiting a pre-configured online shopping or a banking website and choose 'Visit in Secure Shopping Environment' from the alert, the environment will open automatically. The website in the browser chosen as per the Secure Shopping configuration.
- If you are opening the 'Secure Shopping' environment manually, the environment will open with the browser chosen as per the configuration. You can enter the URL of the website in the address bar of the browser.

- The
tools panel at the bottom right of the screen lets you to open the
virtual keyboard, temporarily switch back to your desktop, or to
fully exit the secure shopping virtual environment.
See the explanations given below for more help on the tools panel:
Open applications inside the secure shopping Environment
-
Start the Secure Shopping environment and click the folder icon at bottom-left:
- Browse to the application you want to run and open it
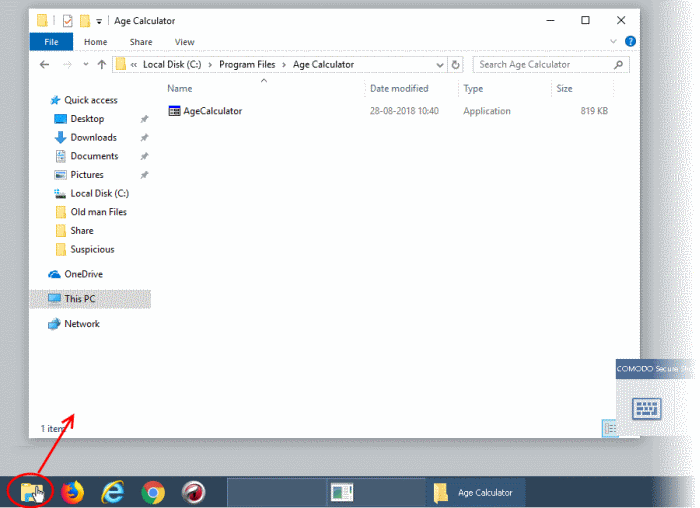
The application will open inside the Secure Shopping environment:
The tools panel at the bottom right of the screen allows you to open the virtual keyboard, temporarily switch back to your desktop, or to fully exit the Secure Shopping virtual environment.
The Tools Panel
The tools panel at the bottom right of the screen allows you to open the virtual keyboard, temporarily switch back to your desktop, or to fully exit the Secure Shopping virtual environment.
The Secure Shopping environment
features an on-screen virtual keyboard that helps you in entering
confidential information like website user-names, passwords and
credit card numbers.
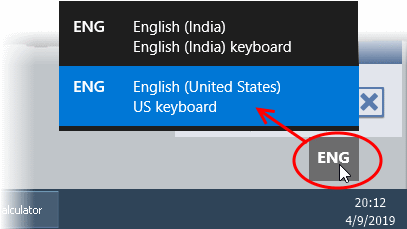
- Click
the language button
 at the bottom-right and select the keyboard
layout you want to use.
at the bottom-right and select the keyboard
layout you want to use.
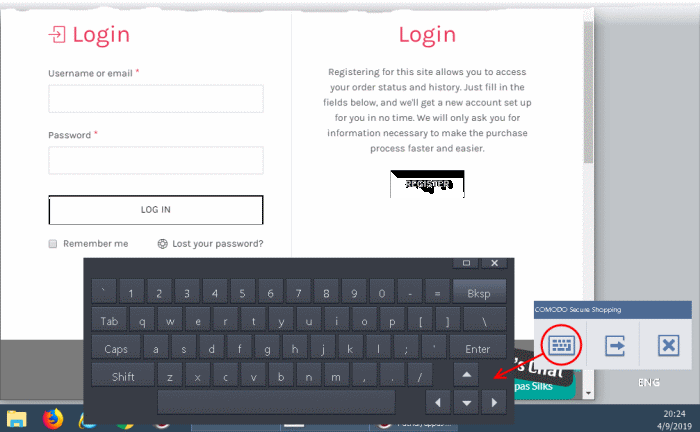
- Click the keyboard icon in the tools panel to open the on-screen virtual keyboard
Temporarily switch to your desktop
- Click
the
 button from the tools pane at the bottom right
button from the tools pane at the bottom right
The Secure Shopping Desktop will be hidden. You can quickly return to it by clicking the button again.
- Click
the 'X' button

A confirmation dialog is shown.
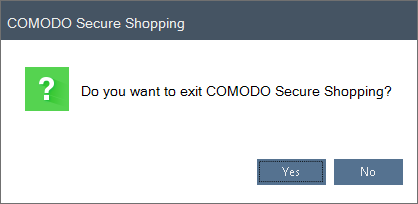
- Click 'Yes' to exit the Secure Shopping environment.



