File Rating Settings
Click 'Settings' > 'File Rating' > 'File Rating Settings'
- A file rating determines how CIS interacts with a file:
- 'Trusted' files are safe to run.
- 'Untrusted' files are malware so they get quarantined or deleted.
- 'Unknown' files are run in the container until they get rated as trusted or untrusted.
- The rating of a file can change over time, especially in the case of 'unknown' files. For example, an 'unknown' file might be re-classified as 'trusted' or 'untrusted' after it has been tested.
- You can also configure whether CIS should auto-upload unknown files to Comodo for analysis.
Open the file rating settings interface
- Click 'Settings' on the CIS home screen
- Click 'File Rating' > 'File Rating Settings':
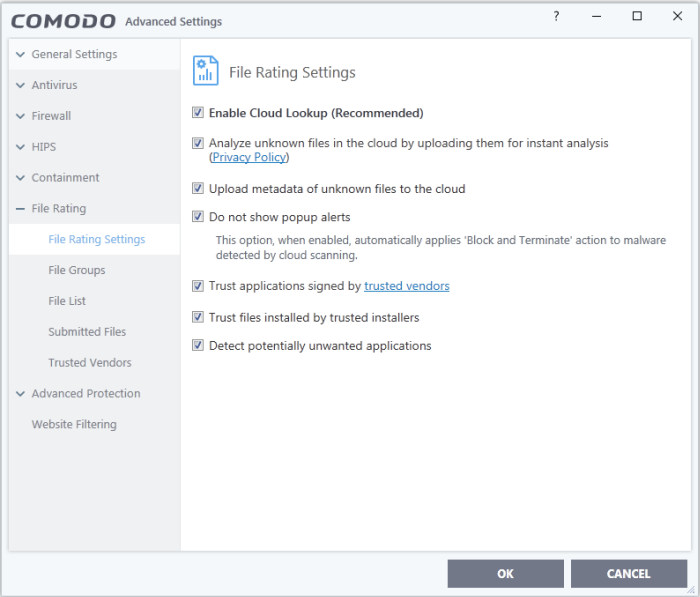
- Enable Cloud Lookup - CIS checks a file's trust rating on our cloud severs as part of the scan process. (Default and recommended = Enabled)
- Analyze unknown files in the cloud by uploading them for instant analysis - CIS uploads files with an 'unknown' trust rating to Comodo for further analysis. Our experts will analyze the file, award it a trust rating, and add it to the global whitelist or blacklist as appropriate. (Default = Enabled)
- Upload metadata of unknown files to the cloud -Metadata is basic file information such as file source, author, date of creation and so on. If enabled, CIS will also send the file metadata when uploading unknown files to Comodo (Default =Enabled)
- Do not show popup alerts – Whether or not CIS should show an alert when an unrecognized or malicious file is detected by the cloud scanner (FLS). (Default = Enabled)
- Enabled - No alerts are shown. This minimizes disturbances but at some loss of user awareness.
CIS will automatically take the following actions based on the file trust rating:
- Unrecognized or Unknown files - These are run in the container as per your auto-containment rules. See Auto-Containment Rules for more details
- Malicious files - Automatically blocked and quarantined
- Disabled - A containment alert is shown for unknown and malicious files
Unrecognized or Unknown files – The following alert is shown:
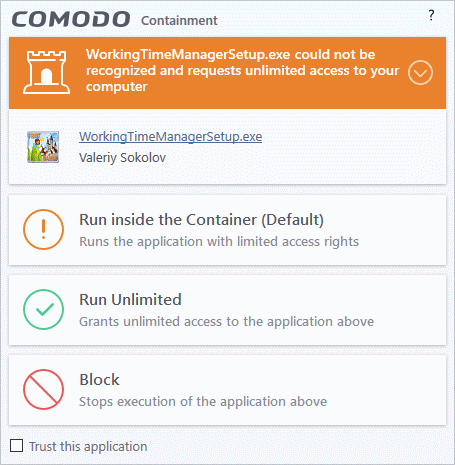
You can choose from these actions:
- Run inside the Container – Executes the program inside the container with limited access rights
- Run Unlimited – Lets the program run as normal on your computer, outside the container. The file is added to the file list as a 'Trusted' file. See File List for more details.
- Block – The program is terminated and not allowed to run.
- Malicious files - The program is automatically blocked and quarantined. You will see the following type of alert:
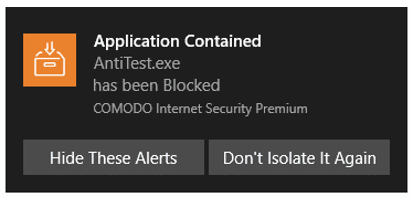
- Don't Isolate It Again – Select this option if you are sure about the trustworthiness of the program / publisher
- The file will be assigned 'Trusted' rating in your local file list, and will be allowed to run without restriction in future. See File List for more details
- Rate applications according to their vendor rating - CIS will give files the same rating as the trust rating of the publisher (software creator). For example - if the vendor is trusted, then all files created by the vendor will be trusted. (Default = Enabled)
- The vendor is the software company who created and digitally signed the file
- You can view vendor trust ratings in 'Advanced Settings' > 'File Rating' > 'Vendor List'
- CIS ships with a list of vendors with 'Trusted' status. You can add new vendors to the list and set your own vendor ratings as required
- Click the 'Vendor Rating' link to open the 'Vendor List' screen. See Vendor List for more details
- Trust files installed by trusted installers - CIS awards trusted status to files whose parent applications are listed in the 'Installer or Updater' rule in HIPS Rules. (Default = Enabled)
- Detect potentially unwanted applications (PUA) - Antivirus scans will flag applications that:
(i) a user may or may not be aware is installed on their computer
(ii) may contain functionality and objectives that are not clear to the user
Example PUA's include adware and browser toolbars.
PUA's are often installed as an additional extra when the user is installing an unrelated piece of software. Unlike malware, many PUA's are legitimate pieces of software with their own EULA agreements. However, the true functionality of the software might not have been made clear to the end-user at the time of installation. For example, a browser toolbar that tells you the weather may also contain code that tracks your online activity. (Default = Enabled)



