Vulnerability Management
- Click 'Applications' > 'Vulnerability Management' to open this interface
- This area lets you view known weaknesses found on your devices, along with their CVE (common vulnerabilities and exposures) rating.
- You can view which devices are affected and install patches as required.
Open the vulnerability management interface
- Click 'Applications' > 'Vulnerability Management'
.png)
There are two tabs, each of which offers a different view of the vulnerabilities:
- Vulnerability List - A list of discovered vulnerabilities and the number of devices affected by each.
Apply corrective patches:
- Click the number in the ‘Target Device Count’ column
- Select the devices you want to patch
- Click the ‘Install Patch’ button above the table
- Vulnerable Devices - A list of devices affected by listed vulnerabilities. Allows you patch affected device with a single click.
- Click 'Applications' > 'Vulnerability Management'
- Click the 'Vulnerability List' tab
.png)
|
Vulnerability List - Column Descriptions |
|
|---|---|
|
Column Heading |
Description |
|
Vulnerability Name |
The vulnerability identifier. This is same as the CVE code. |
|
Vendor |
Developer of the affected software and the corresponding patch. |
|
CVE Addressed |
Identification code of the security threat. Click this to view vulnerability details, vendor and affected devices. |
|
Severity |
Criticality of the vulnerability. The possible levels are:
Examples include remote elevation of privileges exploits that allow attackers to write to the file system, or execute arbitrary code without user interaction. You should patch critical vulnerabilities as soon as possible.
|
|
Target Device Count |
Number of devices affected by the vulnerability. Click this to view device details and implement patches. |
- Click the funnel icon to filter vulnerabilities by various criteria
-
Click a column header to sort in ascending / descending / alphabetical order
From this interface you can:
View Details of a Vulnerability Threat
- Click 'Applications' > 'Vulnerability Management' then the 'Vulnerability List' tab
- Click the CVE ID number in the CVE Addressed column
The CVE details has three tabs, General, Vendor and Devices. By default the general tab is open in the CVE details screen.
- General - Provides the CVE details such as the name of the vulnerability type, published date and so on.
Click the vendor tab.
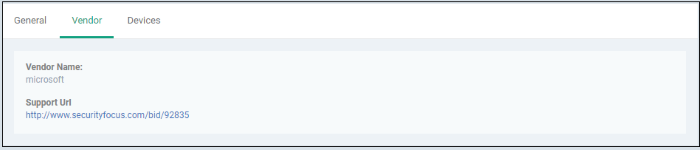
- Vendor Name - The software publisher's name
- Support URL - Clicking the link will take you to the technical community page that provides full information about the vulnerability, discussions, solutions and so on
Click the devices tab.
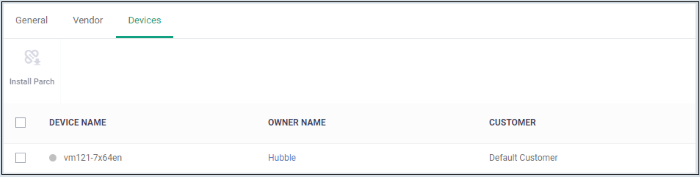
-
Shows the affected devices. You can run security patches for devices from here. See 'Run a Security Patch on Devices'
Run a Security Patch on Devices
You can run security patches targeted to address a particular CVE security threat.
- Click 'Applications' > 'Vulnerability Management' then the 'Vulnerability List' tab
- Click the number in the target device count column or click the CVE ID number in the CVE Addressed column then the 'Devices' tab
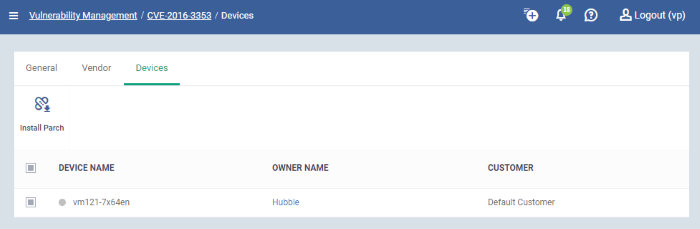
- Device Name - Clicking the name will take you to the patch management section in the device summary page
- Owner Name - Clicking the name will take you to user information page
- Customer - The name of the organization the device is assigned to
- Select the device and click 'Install Patch' above
A confirmation message is shown:
Export Vulnerability List
- Export the list of files to a CSV file as follows:
- Click 'Application' > 'Vulnerability Management' > 'Vulnerability List'
- Click the 'Export' button above the table then choose 'Export to CSV':
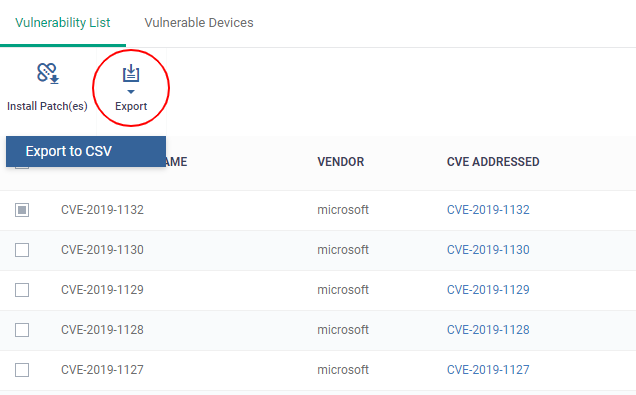
- The CSV file will be available in 'Dashboard' > 'Reports'
- See Reports in The Dashboards for more details.
This screen lets you view devices that are affected by vulnerabilities and install patches as required. The ‘Install Patches’ button will install every required patch.
- Click 'Applications' > 'Vulnerability Management' then the 'Vulnerable Devices' tab
.png)
- Device Name - Affected device. Click the name to view the patches available for the device.
- Owner Name - User of the device. Click the name to view the user’s details.
- Customer - The name of the organization to which the device is assigned.
- Click a column header to sort in ascending / descending / alphabetical order
Install security patch(es)
-
Select the devices you want to patch then click the ‘Install Patch(es)’ button.
You will see the following confirmation message:

All available patches are installed.
Export the list of Vulnerable Devices
- Export the list of files to a CSV file as follows:
- Click 'Application' > 'Vulnerability Management' > 'Vulnerable Devices'
- Click the 'Export' button above the table then choose 'Export to CSV':
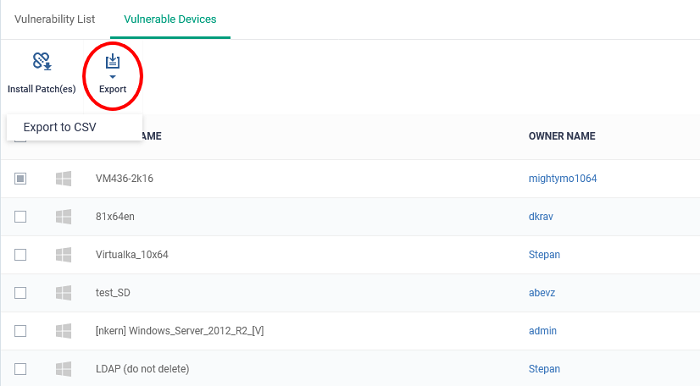
- The report will exported in CSV format the file available in 'Dashboard' > 'Reports'
- See Reports in The Dashboards for more details.



