View Reports
Reports gives a comprehensive view of security checks that are used to detect misconfigured and vulnerable assets. These assets are scanned by tools like Stig, Prowler, Nipper, SecurityHub, etc. to find misconfigurations and vulnerabilities with respect to compliance frameworks (PCI-DSS, NIST, GDPR, SOC2, HIPAA, etc.). The security checks are in accordance with compliance frameworks to ensure the security of sensitive data. These checks are divided into different sections, namely identity and access management, Logging, Monitoring, Networking and Storage.
- Click 'Security' > 'Cloud Security'
- Click 'Reports'
Open the Reports Interface
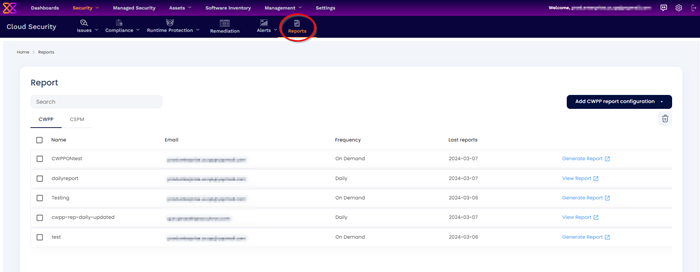
The interface has two tabs:
The cloud workload protection platform, or CWPP, is a solution developed to secure workloads.
The following details on mentioned in the report
- List of workloads with no protection - This will provide list of workloads where there is no policy applied
- List of workloads with policy violation - This will provide list of workloads where their policy is applied
- Cluster Security trend - This will show cluster security trend graph
- Compliance Trend - This will show compliance trend graph
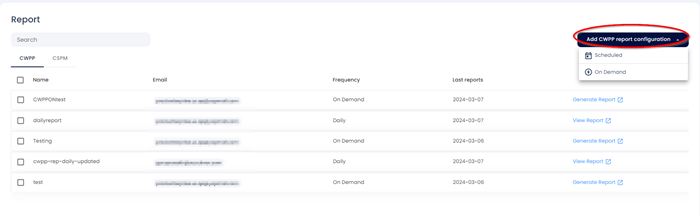
A CWPP Report Configuration have 2 types
- Scheduled - These reports are automatically generated at frequency you choose.
- On Demand – Manually generated reports when needed
To create a Scheduled report, please provide following details
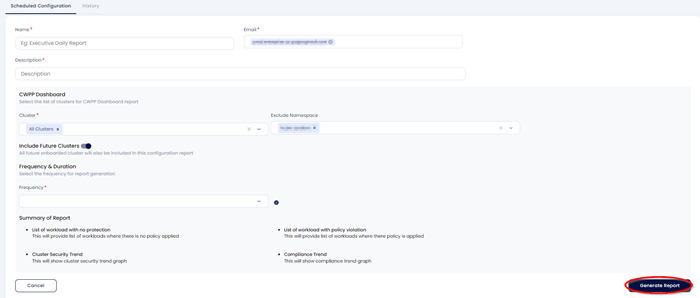
Name – Name of the report
Email – Email of the person who created the report
Description – Description about the report
Cluster – Select Cluster to include in the report
Exclude Namespace – You can exclude namespace which are not to be added in the report
Frequency – Frequency of the report to be generated
To create a On Demand report, please provide following details
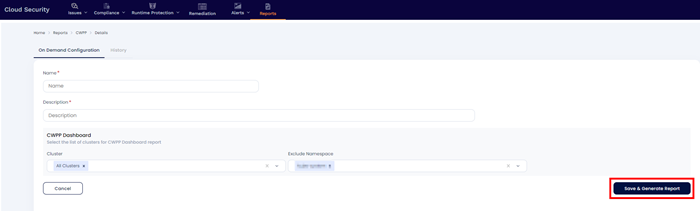
Name – Name of the report
Description – Description about the report
Cluster – Select Cluster to include in the report
Exclude Namespace – You can exclude namespace which are not to be added in the report
The Cloud Security Posture Management, or CSPM, is the process of monitoring cloud-based systems and infrastructures for risk and misconfigurations.
Reports gives a comprehensive view of security checks that are used to detect misconfigured and vulnerable assets. These assets are scanned by tools like Stig, Prowler, Nipper, SecurityHub, etc. to find misconfigurations and vulnerabilities with respect to compliance frameworks (PCI-DSS, NIST, GDPR, SOC2, HIPAA, etc.). The security checks are in accordance with compliance frameworks to ensure the security of sensitive data. These checks are divided into different sections, namely identity and access management, Logging, Monitoring, Networking and Storage.
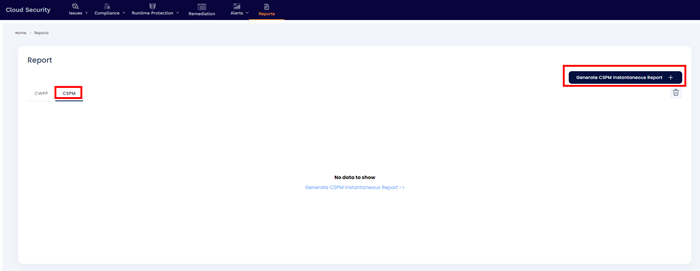
Generate CSPM Instantaneous Report
A CSPM report can be generated instantaneous with following details
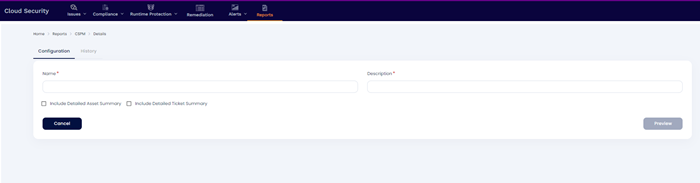
Total Cloud Accounts – Total number of cloud accounts that were scanned
Total Findings - Total number of vulnerabilities and misconfigurations detected.
Checks Passed - Total number of checks that passed or failed the guidelines set by the compliance framework
Total Assets with Findings – Total number of assets which have vulnerabilities or misconfigurations.
Overall Compliance Percentage – Total percentage after running Compliance test
Assets Summary - Assets status is categorised by result and top 10 assets with failed checks
Asset Detailed Reports – Total number of assets with failed result and its checks
Region Based Findings – Findings are categorized based on the regions
Ticket Summary – Number of tickets created after findings
Ticket Detailed Summary – Detailed summary of created tickets with date, status and its priority.



