View Alerts and Security Events
-
Click 'Security' > 'Endpoint Security' > 'Alerts'
The 'Alerts' interface shows a list of all security alerts and events on managed endpoints.This includes events from the antivirus, containment, application-control, autorun control, virtual desktop and EDR components.
-
You can also configure Xcitium to send automated notifications emails to selected recipients whenever an alert is generated or a security event is logged. See Alert Notification Settings for help to do this.
-
To view threats recorded on Android devices, go to 'Security' > 'Endpoint Security' > 'Antivirus' > 'Android Threat History'.
Xcitium retains security event logs for 12 months
for PCI-DSS compliance.
Events that are captured include:
Antivirus- Windows, Mac OS, and Linux devices
-
File blocked, moved to quarantine, or ignored
-
File restored/removed from quarantine
-
File skipped by a virus scan
-
File rated as trusted, or submitted as a false positive, at the scan results screen
-
File added to the exclusions list
Containment- Windows devices
-
File blocked, ignored, or run in the container by:
Auto-containment rules in the profile on the device
A local user running the file in the container on a one-off basis
Application Control - Windows devices
-
Unrecognized or malicious file added to, or removed from, the XCS 'File list'.
Changes to the trust rating of a file
See Manage File Trust Ratings on Windows Devices for more details.
Autoruns Control - Windows devices
-
Records the action taken by XCS on apps that try to modify Windows services, startup entries, and scheduled tasks. Recorded actions include:
Ignore
Terminate
Terminated and disabled
Quarantined and disabled
Restored
Deleted
Virtual Desktop - Windows devices
-
Virtual desktop activity on endpoints. Recorded actions include:
- Launched
Terminated
Session started
Session paused
Session continued
Session terminated
Switched to host
Switched to virtual desktop
EDR - Windows devices
-
Security events identified by EDR security policy
-
EDR ships with a default security policy with pre-defined rules
-
The rules determine which events will generate an alert.
-
There are seven categories of rules:
Process Events - Rules to generate alerts when processes are invoked by an application.
Registry Events - Rules to generate alerts about changes to the Windows registry on your endpoints.
File Events - Rules to generate alerts about modifications to system files.
Download Events - Rules to generate alerts when files are downloaded via browsers, emails, shared folders or external drives.
Upload Events - Rules to generate alerts when files are transferred to shared folders or external drives.
Defense+ Events - Rules to generate alerts when processes attempt to access critical operating system functions or launch attacks.
Network Events - Rules to generate alerts about any service listening to ports and network connections on your endpoints.
See Appendix 3: Default Xcitium Security Policy Details for full list of rules in the Xcitium default security policy.
The interface also lets you rate files, view file details, and move files in or out of quarantine.
View alerts and security events
-
Click 'Security' > 'Endpoint Security'
-
Click the 'Alerts' tab
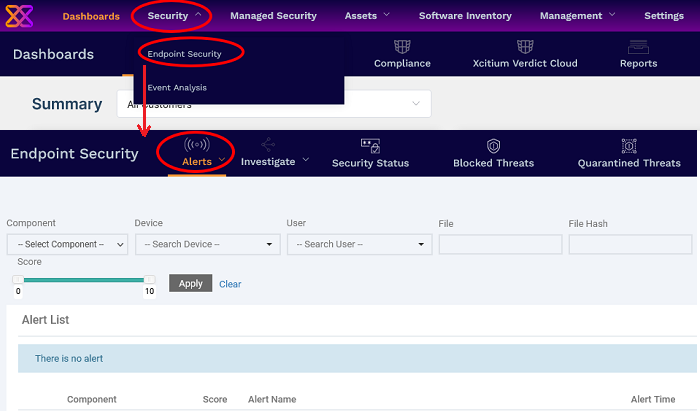
You can view the 'Alerts' interface in three ways:
-
Alert Search - Shows alerts and events in chronological order. You can search for specific events using various filter parameters. See View Security Alerts and Events by Time for more details.
-
Hash View - All alerts and events concerning a particular file are grouped together. The interface also lets you assign a trust rating to files based on your assessment. See View Alerts and Security Events by Files for more details.
-
Device View - Shows all alerts and events that occurred on a specific device. See View Security Alerts and Events by Device for more information.



