Script Analysis Settings
-
XCS can analyze code in executable files in two ways:
Heuristic command line analysis
Embedded Code Detection
-
You can enable these features and select the programs you want to monitor by adding a 'Script Analysis' section to a profile.
-
You can also monitor programs which try to make changes to auto-run entries, Windows services and scheduled tasks.
|
Background: Heuristic command line analysis:
Embedded code detection:
For example, the program wscript.exe can be made to execute visual basic scripts (.vbs file extension) via a command similar to 'wscript.exe c:/tests/test.vbs'. If this option is selected, XCS detects c:/tests/test.vbs from the command-line and applies all security checks to this file.
|
Configure 'Script Analysis' Settings
-
Click 'Assets' > 'Configuration Templates' > 'Profiles'
-
Open the Windows profile you want to work on
Click the 'Script Analysis' tab then 'Edit', if it has already been added to the profile
OR
Click 'Add Profile Section' > 'Script Analysis' if it hasn't yet been added
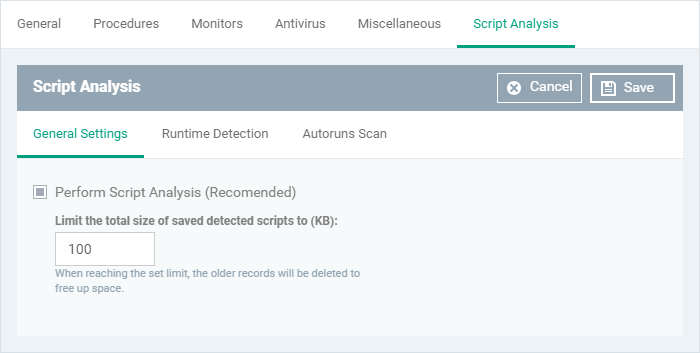
The 'Script Analysis' settings screen contains three tabs:
-
General Settings - Enable script analysis and set the maximum file size which should be checked.
-
Runtime Detection - Select which programs are monitored throughout their operation.
-
Autoruns Scan - Choose programs that you want to monitor to see if they make changes to auto-run entries, Windows services and scheduled tasks.

-
Perform Script Analysis - Enable/Disable script analysis. XCS will only analyze the applications selected in the 'Runtime Detection' tab if this option is enabled. An alert is generated if malicious code is found in any item. (Default = Enabled)
-
Limit the total size of saved detected scripts to - XCS stores scripts run by managed applications for analysis. This option lets you specify the total size of stored scripts. When the set limit is reached, the older scripts are deleted automatically. (Default = 100 KB)
-
Lets you select executables which should be analyzed during their execution.
-
You can also add custom applications which you want to protect.
-
Click the 'Runtime Detection' tab in the 'Script Analysis' settings interface
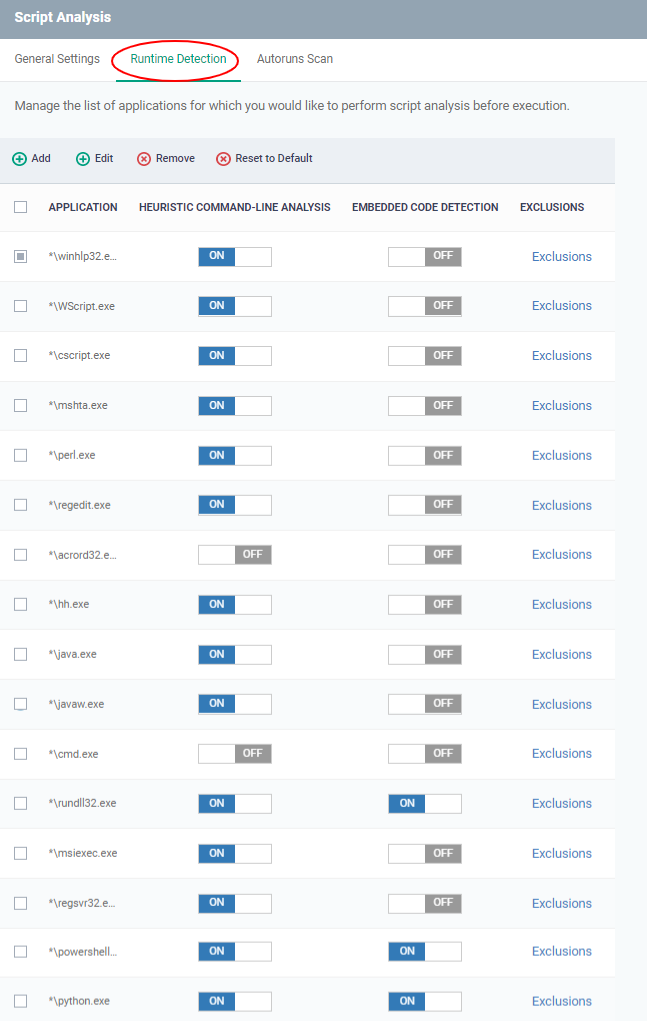
Use the switch in the 'Heuristic Command-Line Analysis' column to enable/disable heuristic command line analysis for each application.
Use the switch in the 'Embedded Code Detection' column to enable/disable embedded code detection for each application.
-
Select an application and click the edit button to update its details.
-
Select an application and click the trash can icon to remove it from the list.
- Click Script Analysis > Runtime Detection > Exclusions
- Select an application to which you need to add an exclusion
- Click 'Add' .Enter a regex, and click 'Ok' to save your changes
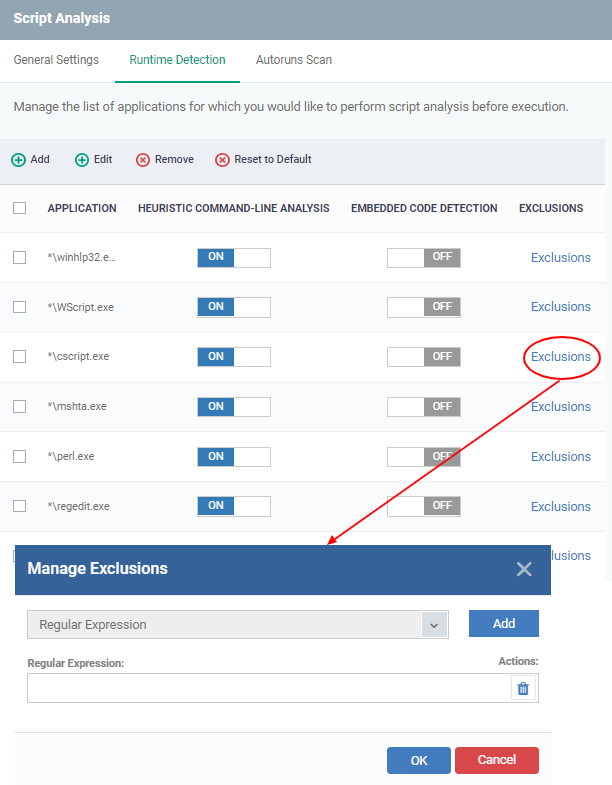
- This feature will exclude and log the command line detected by script analysis by defining a regular expression.
- For ex : If a malware script in the comment statement contains something that matches exclusion, that will be vulnerability and lauched .This functionality will allow to create malware that are focused on XCS.
- To delete the added regex click the delete icon, and then selected regular expression will be removed.
-
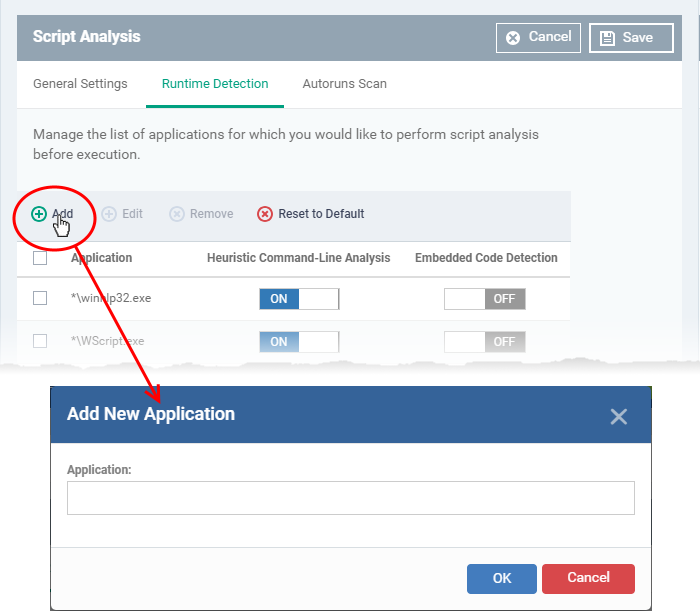
Click 'Add' at the top to include a new application to the list.
-
Enter the name of the application in the 'Add Application' dialog and click 'Add'.
-
The new application will be added to the list and will be selected by default. You can use the toggle switch beside it to enable/disable it at any time.
-
Repeat the process to add more applications
-
To reset the list to the default list of applications, click 'Reset to Default' on the top
-
Click 'OK' to apply your changes.
-
Select applications which should be monitored in case they make changes to autoruns, Windows services or scheduled tasks.
-
You can also add custom applications which you want to monitor.
-
Click the 'Autoruns Scan' tab in the 'Script Analysis' settings interface
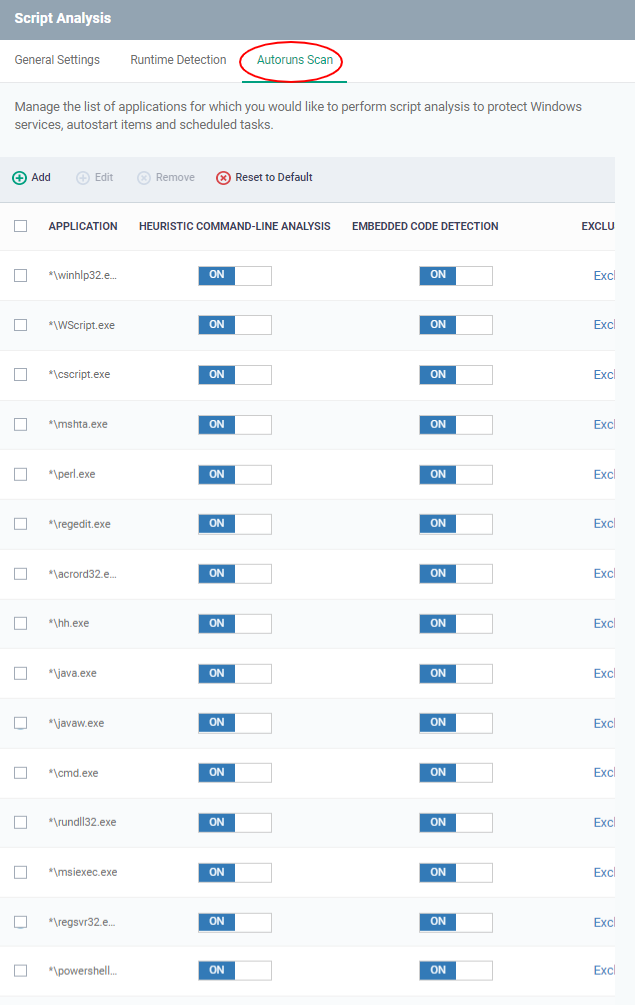
Use the switch in the 'Heuristic Command-Line Analysis' column to enable/disable heuristic command line analysis for each application.
Use the switch in the 'Embedded Code Detection' column to enable/disable embedded code detection for each application.
-
Select an application and click the edit button to update its details.
-
Select an application and click the trash can icon to remove it from the list.
- Click Script Analysis > Autoruns Scans > Exclusions
- Select an application to which you need to add an exclusion
- Click 'Add' .Enter a regex, and click 'Ok' to save your changes
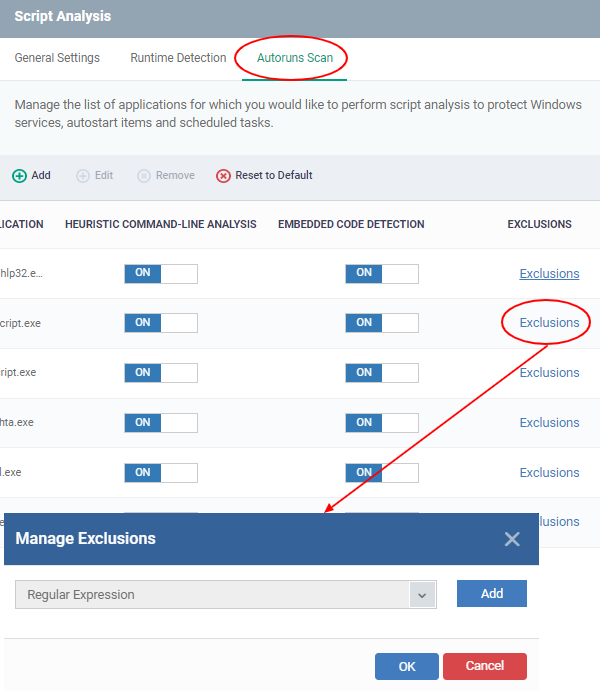
- You can exclude and log the command line detected by script analysis by defining a regular expression. The detected but excluded items shall be able to log as 'ignored'.
- Click ‘Add’ to enter a new regular expression.
-
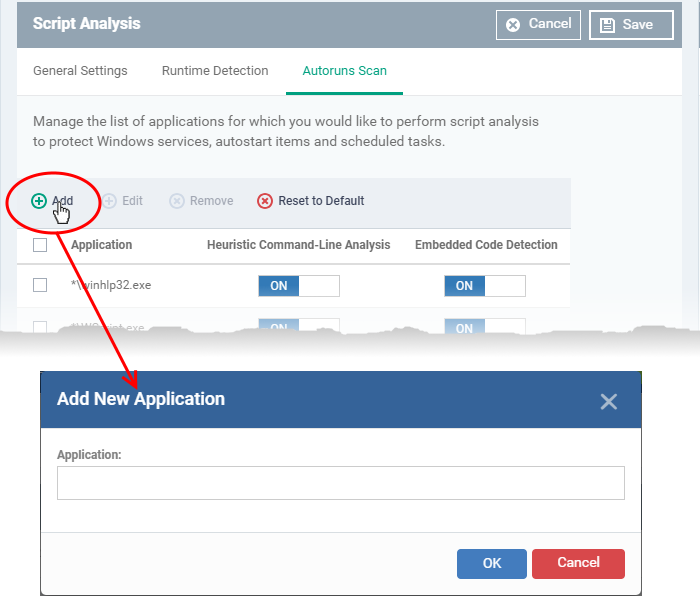
Click 'Add' at the top to include a new application to the list.
-
Enter the name of the application in the 'Add Application' dialog and click 'Add'.
-
The new application will be added to the list and will be selected by default. You can use the toggle switch beside it to enable/disable it at any time.
-
Repeat the process to add more applications
-
To reset the list to the default list of applications, click 'Reset to Default' on the top
-
Click 'OK' to apply your changes.
-
Click 'Save' at top right to apply your settings to the profile.



