View Android Threat History
Click Security' > 'Endpoint Security' > 'Investigate' > 'Android Threat History'
-
The threat history area is a record of all malicious events on your Android devices since you deployed Xcitium.
-
The Android threat history list shows old events caused by malware which has been removed, and new events by malware which is still present.
-
Xcitium retains logs of malicious events for 12 months for PCI-DSS compliance.
-
You can remove unnecessary entries from the list as required
View Android threat history
-
Click Security' > 'Endpoint Security' > 'Investigate' > 'Android Threat History'
-
Click the 'Android Threat History' tab.
Select a group to view events on its devices
Or
Select 'Show All' on to view events on all devices added to Xcitium
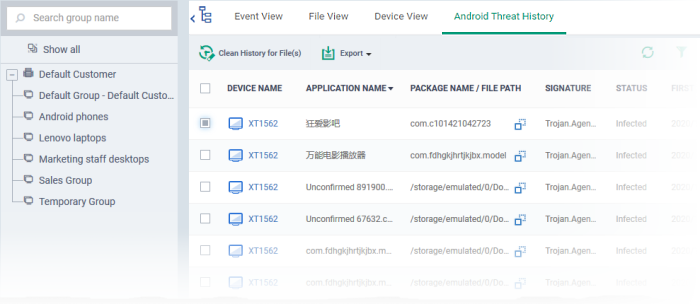
|
Column Heading |
Description |
|---|---|
|
Device Name |
The label assigned to the device. If no name was assigned by the end-user, the model number of the device is used. A gray text color indicates the device has been offline for the past 24 hours.
|
|
Application Name |
The name of the infected application. |
|
Package Name / File Path |
Malware detected on installed application - Shows the package name Malware detected in APK file system - Shows the file path to the app |
|
Signature |
The name of the identified malware. |
|
Status |
Whether the malware was uninstalled, yet to be uninstalled or ignored. |
|
First Detection |
Date and time of the scan which first discovered the malware on the device. |
|
Last Detection |
Date and time of the last scan to discover the malware. |
Remove unwanted entries from the Android threat history interface
-
Select the log entries you want to remove then click 'Clean History for File(s)' at the top
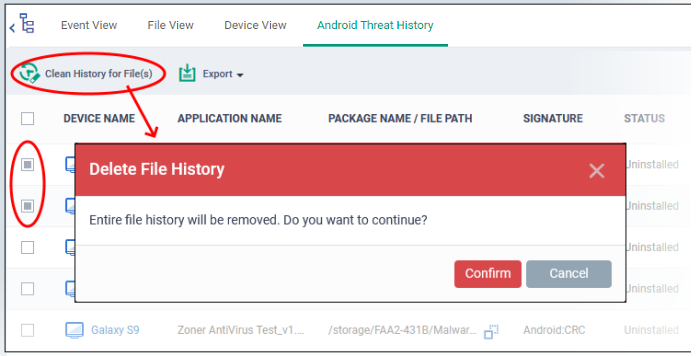
-
Click 'Confirm' to remove the entries from the list
-
Deleting file history will only remove the log entry. The file is not removed from the device or from any other interfaces in which it is listed (for example, the quarantine list).
Sorting, Search and Filter Options
-
Click any column header to sort items in ascending/descending order of the entries in that column
-
Click the funnel icon
 on the right to filter items by various criteria,
including by OS, device name, application name, package name/file
path, signature, status and first/last detection dates.
on the right to filter items by various criteria,
including by OS, device name, application name, package name/file
path, signature, status and first/last detection dates.
-
Start typing or select the search criteria in the search field to find a particular item and click 'Apply'
-
To display all items again, clear any filters and search criteria and click 'Apply'.
Export threat history records as a CSV file
-
Click Security' > 'Endpoint Security' > 'Investigate' > 'Android Threat History' tab
-
Click the funnel icon
 to filter which records are included in the report.
to filter which records are included in the report.
-
Click the 'Export' button and choose 'Export to CSV':
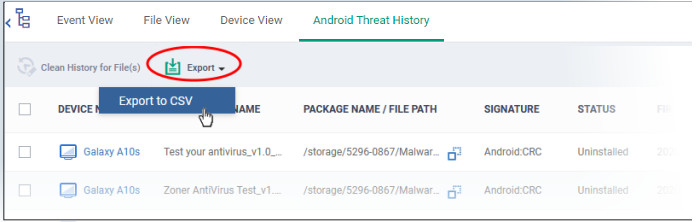
The report is generated in .csv file format.
-
Click 'Dashboard' > 'Reports' to view the report. See Reports if you need more help with this interface.



