DLP Logs
Click 'Security' > 'Endpoint Security' > 'Data Loss Prevention' > 'Logs'
-
The logs tab shows DLP events on endpoints.
-
Log details include the name of the file, its location on the device, the rule that discovered the file, and the type of sensitive information in the file.
-
You can use the 'Remote Tools' feature to connect to the target device and access the files at the path provided. You can then move/ remove/ edit file permissions as required.
View DLP scan logs
-
Click 'Security' > 'Endpoint Security' > 'Data Loss Prevention'
-
Select the 'Logs List' tab
Select a group to view only the DLP logs from the devices in that group
Or
Select 'Show all' to view DLP logs from every device enrolled to Xcitium
-
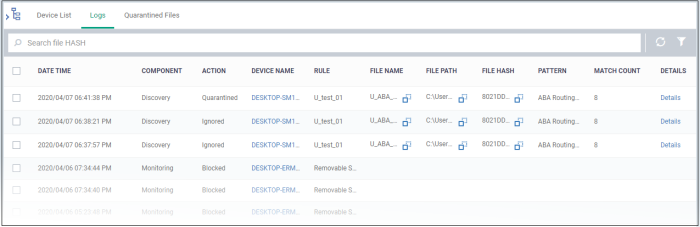
The interface shows all monitoring and discovery rule events:
|
Column Heading |
Description |
|---|---|
|
Date Time |
The date and time the file was discovered |
|
Component |
The type of rule that generated the log. This can be either a discovery rule or a monitoring rule. |
|
Action |
The XCS response when the rule was triggered. You can use the remote tools feature to access and take actions on files found by discovery rules. See Remotely Manage Folders and Files on Windows Devices for help to do this. |
|
Device Name |
The affected endpoint.
|
|
Rule |
The name of the DLP rule for which the event is logged. |
|
File Name - Discovery rule only |
The file in which sensitive data was found.
|
|
File Path - Discovery rule only |
The location of the file on the device.
|
|
File Hash |
The SHA1 hash value of the file.
|
|
Pattern - Discovery rule only |
The type of data contained in the file. For example, 'Name + Social Security Number'. |
|
Match Count - Discovery rule only |
Number of instances of the pattern that were found in the file. |
|
Details - Discovery rule only |
Click this to view the sensitive file found on the endpoint. See below for an example. |
-
Click the details link in a discovery rule log row
-
An example of file details is shown below:
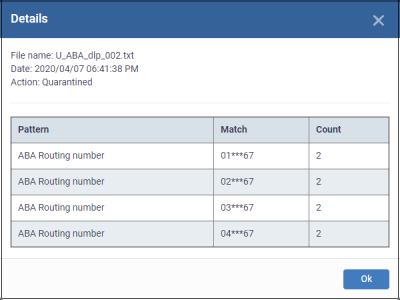
The 'match' column shows the first and last two characters of the discovered data. The option to show this should be enabled in the discovery rule.
-
Click 'Ok' to return to logs screen.
Take action on the files
After identifying sensitive information, there are two ways you can connect to the device to manage the files:
-
Xcitium Enterprise console – Click 'Assets' > 'Devices' > 'Device List' > select a running Windows device > Click 'Remote Tools' > 'File Explorer'.
See Remotely Manage Folders and Files on Windows Devices for help to do this.
-
Remote Control app – Click 'Assets' > 'Devices' > 'Device List' > 'Device Management' > select a Windows device > Click the 'File Transfer' button.
You need to download and install the remote control app to do this
See Transfer Items to / from the Remote Computer for help to do this.



