View Vulnerabilities findings
Xcitium Cloud Security Posture Management tool identifies the vulnerabilities in the cloud assets and images present in the registries once it is onboarded into the SaaS. It automatically scans these Assets and registries with help of various open-source tools. It uses tools like Clair, Trivy, CLOC, Fortify, Snyk, SonarQube, Cloudsploit, Kube Bench, and various other open-source tools for Scanning. The scanned results and findings are parsed with the help of parsers and vulnerabilities are populated in the dashboard.
- Click 'Security' > 'Cloud Security'
- Select 'Issues' > 'Vulnerabilities'
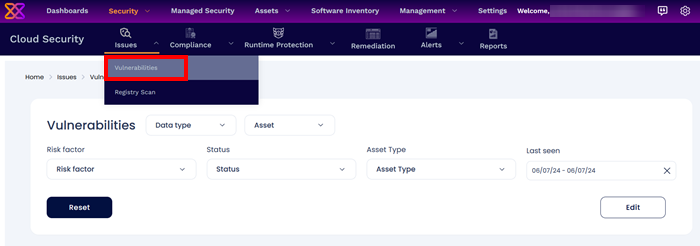
The interface explains you:
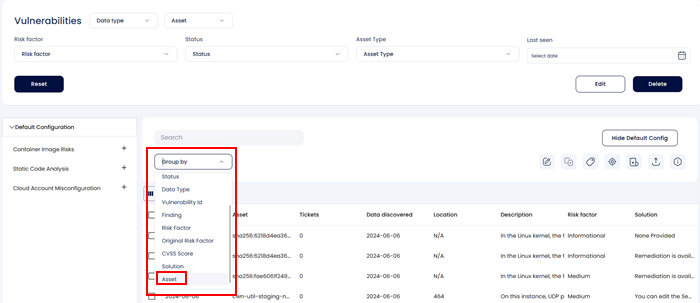
Findings can be grouped according to the tools that were used to do the scan by selecting the "Data Type" option from the "Group By" drop down in the Vulnerabilities screen.
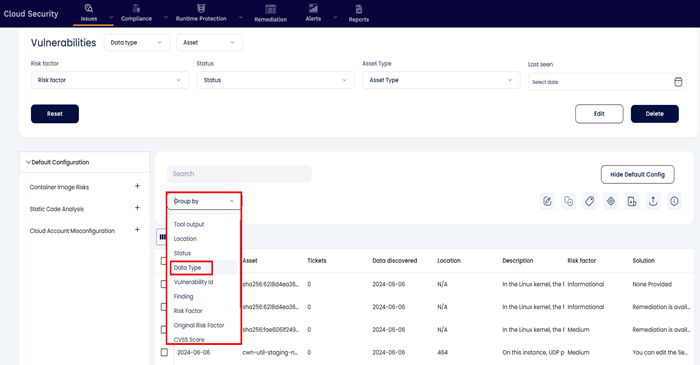
Users can further filter the findings with respect to their Risk factor so that they can have a view of the most critical findings from each tool being used.
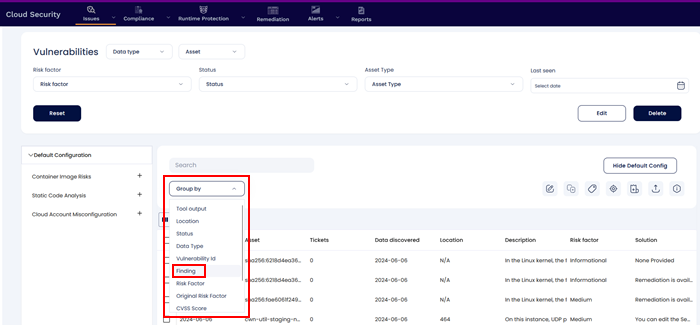
When resolving and patching vulnerabilities it is important to tackle the findings that are most abundant and most severe first. Users can use the Group by Findings feature to look for the vulnerabilities or misconfiguration that exist in large no. of assets and prioritize them accordingly.
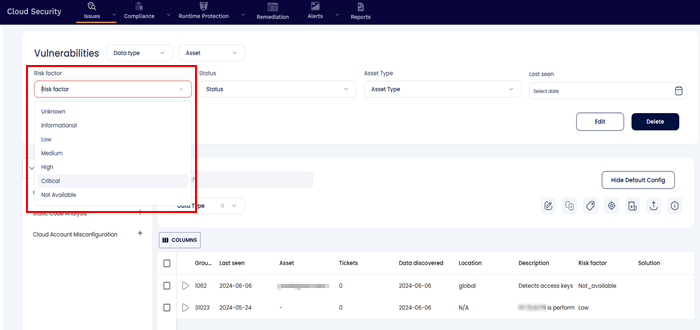
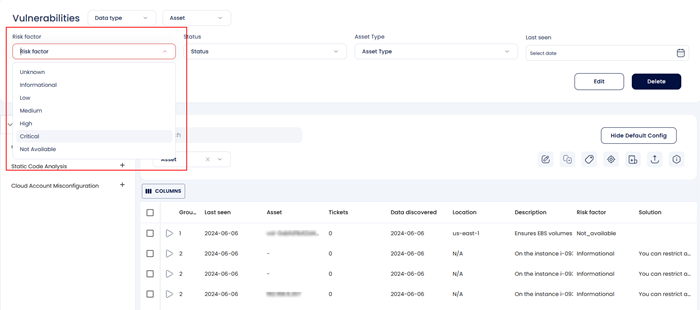
Further users can select the Risk Factor to filter the findings based on their severity. This again narrows the findings that need to be remediated.
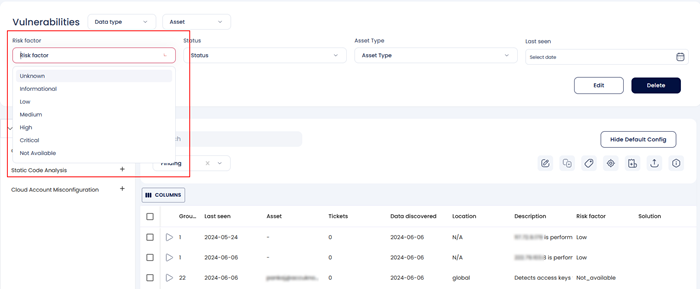
Users can have an Asset wise view of the findings. Grouping by assets, groups the vulnerabilities or misconfigurations together with respect to the asset with which they are associated.
If coupled with the Risk factor filter, users can have a view of the most critical assets i.e., the assets that have the most no. of critical findings.
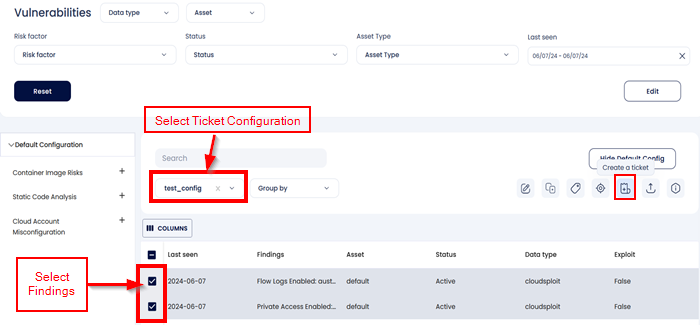
Xcitium enables customers to manage vulnerabilities/findings through auto-creation of tickets on bulk of security findings of similar kind. To create tickets, select a set of findings, select the ticketing configuration, and click create ticket.
Similarly, the same steps can be followed for creating tickets in asset groupings, click on the desired asset and scroll down to the vulnerabilities section and do the steps.
| Note: Selection of Ticket Configuration option enables only when Jira or any other ticketing backend is configured under Settings > Cloud Security settings > Integrations > CSPM > Add connector. Also, while creating the ticket configuration, the default template should have Vulnerability (Group by Finding) selected. |



